First make sure certbot is installed on your system, the instructions below assume that you’re using Ubuntu.
If you just want to create the Certificate, skip to Step 2.
Step 1: Installing Certbot
First you’ll need to add the repository:
$ sudo add-apt-repository ppa:certbot/certbot
After that run update:
$ sudo apt-get install certbot
Now that certbot is all installed, it’s time for the certificate.
Step 2: Generate The Wildcard Certificate
certbot certonly \
--manual \
--preferred-challenges=dns \
--email letsencrypt@example.com \
--server https://acme-v02.api.letsencrypt.org/directory \
--agree-tos \
-d *.example.com
Step 3: Verify Domain Ownership
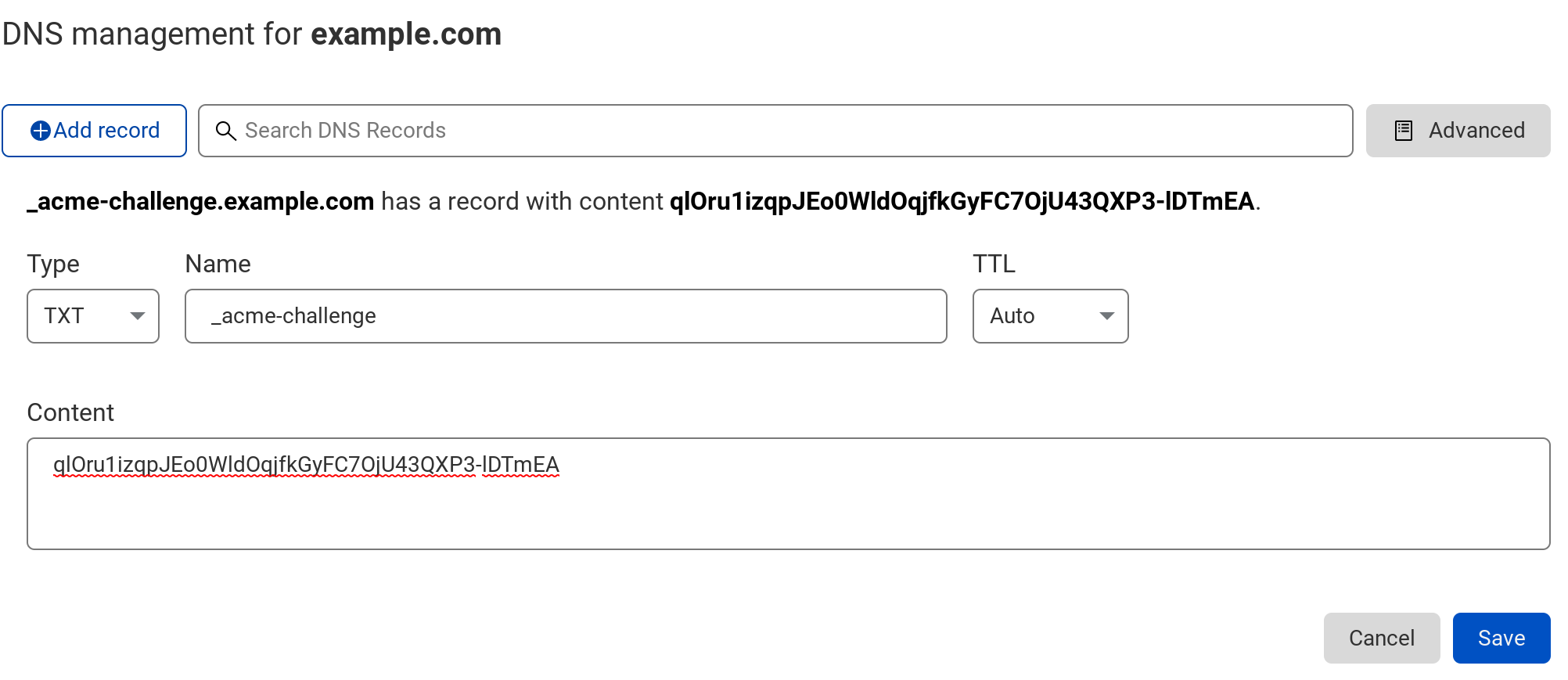
After executing the above step, Certbot will ask you to create a DNS text record.
Please deploy a DNS TXT record under the name
_acme-challenge.example.com with the following value:
qlOru1izqpJEo0WldOqjfkGyFC7OjU43QXP3-lDTmEA
Before continuing, verify the record is deployed.
Create the record and then use dig to verify that the record is working:
dig _acme-challenge.example.com txt
It should return something that looks like this:
;; ANSWER SECTION:
_acme-challenge.example.com. 300 IN TXT "qlOru1izqpJEo0WldOqjfkGyFC7OjU43QXP3-lDTmEA"
After it’s properly working hit enter to continue.
Step 4: Get the Certificate
After hitting enter on the above step your terminal window should now look something like this:
Press Enter to Continue
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/example.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/example.com/privkey.pem
Your cert will expire on 2020-08-22. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
...
You can also verify what certificates you have with certbot:
certbot certificates
This will output a list of currently installed certificates:
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Found the following certs:
Certificate Name: example.com
Domains: *.example.com
Expiry Date: 2020-08-22 18:11:07+00:00 (VALID: 89 days)
Certificate Path: /etc/letsencrypt/live/example.com/fullchain.pem
Private Key Path: /etc/letsencrypt/live/example.com/privkey.pem
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you have any questions or would like further support, please use my contact form.
